
In my previous blog, I introduced the concept of Decoy Data—encrypting real personally identifiable information (PII) and swapping it out for convincing fakes. While my research turned up plenty of articles about decoys and honeypots luring cybercriminals into traps, I haven’t seen this exact approach in practice.
Let’s be clear: this isn’t a replacement for solid, well-implemented security. Think of it as another instrument in your security orchestra. It works on the principle of deception—giving attackers something to find, but never the actual treasure.
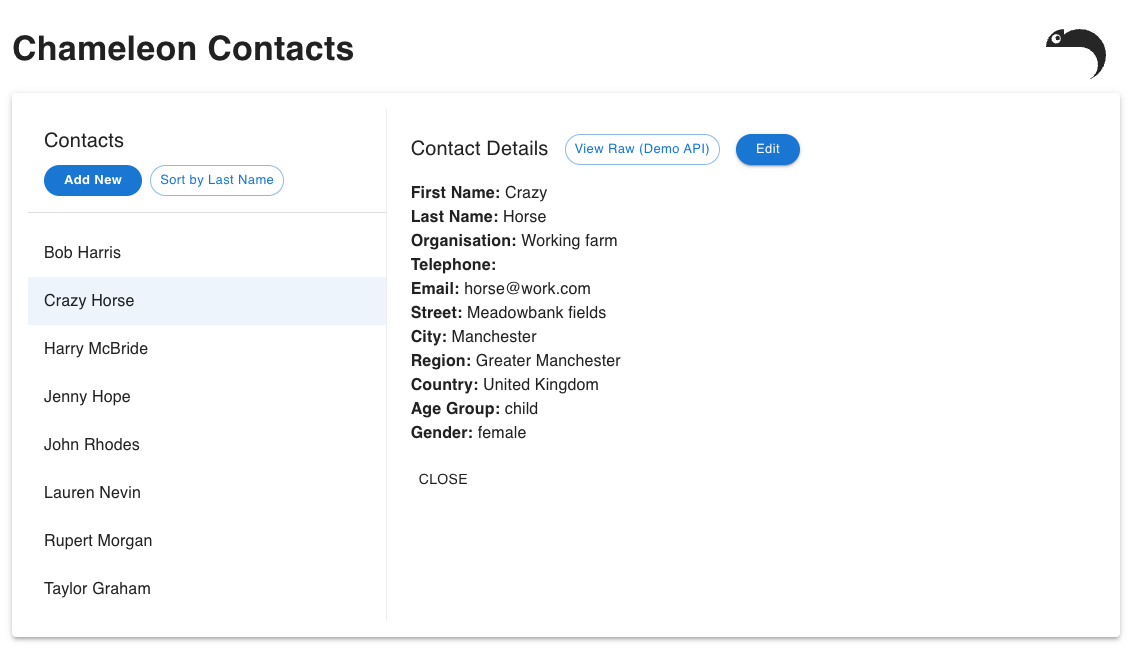
For my proof of concept, I built a simple address book application. (Curious about the code? Check out Chameleon Contacts.) Chamelon Contacts
Here’s how the decoy data model breaks down:
-
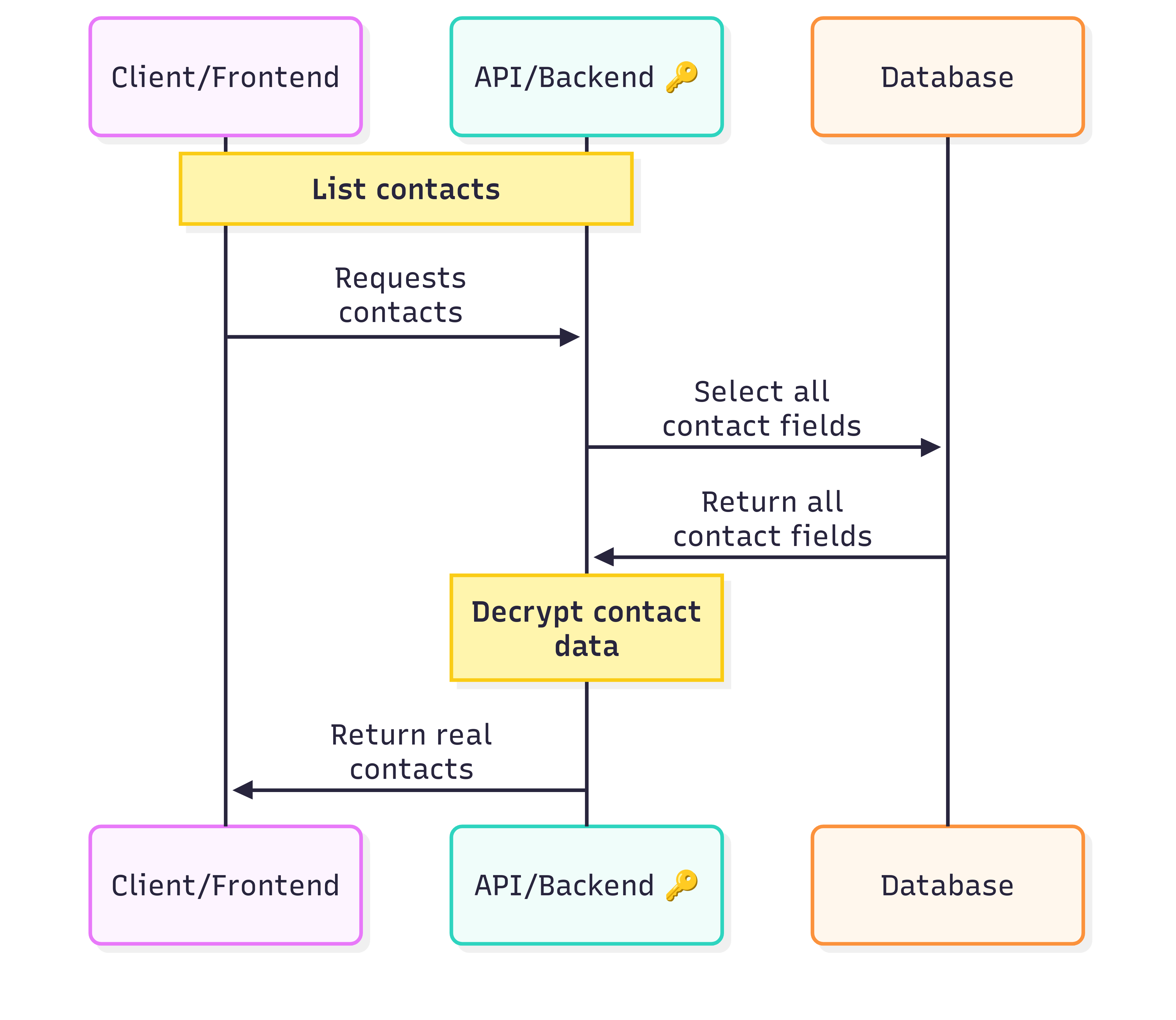
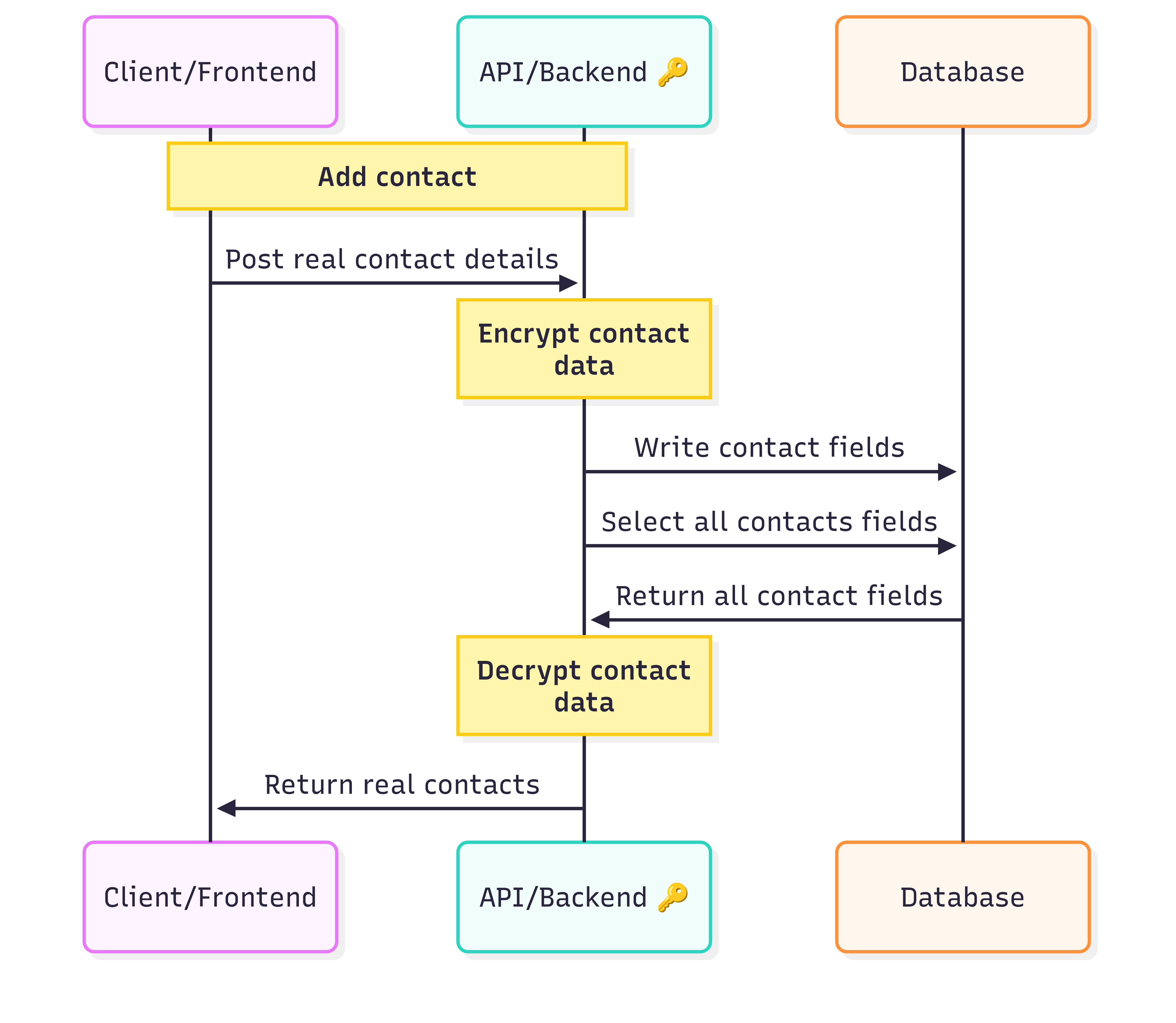
Client/Frontend:
The user-facing side only deals with genuine data. It’s blissfully unaware of any encryption magic happening behind the scenes. -
API/Backend:
Serving as the bridge between frontend and database, the backend handles all encryption, decryption, and CRUD operations. It’s the gatekeeper—the only part with access to encryption keys. -
Database:
The database stores both encrypted real data and plausible fakes. Importantly, it has no access to the keys.
When you request a list of contacts, the process flows smoothly between these components, and you see the correct details in the app.
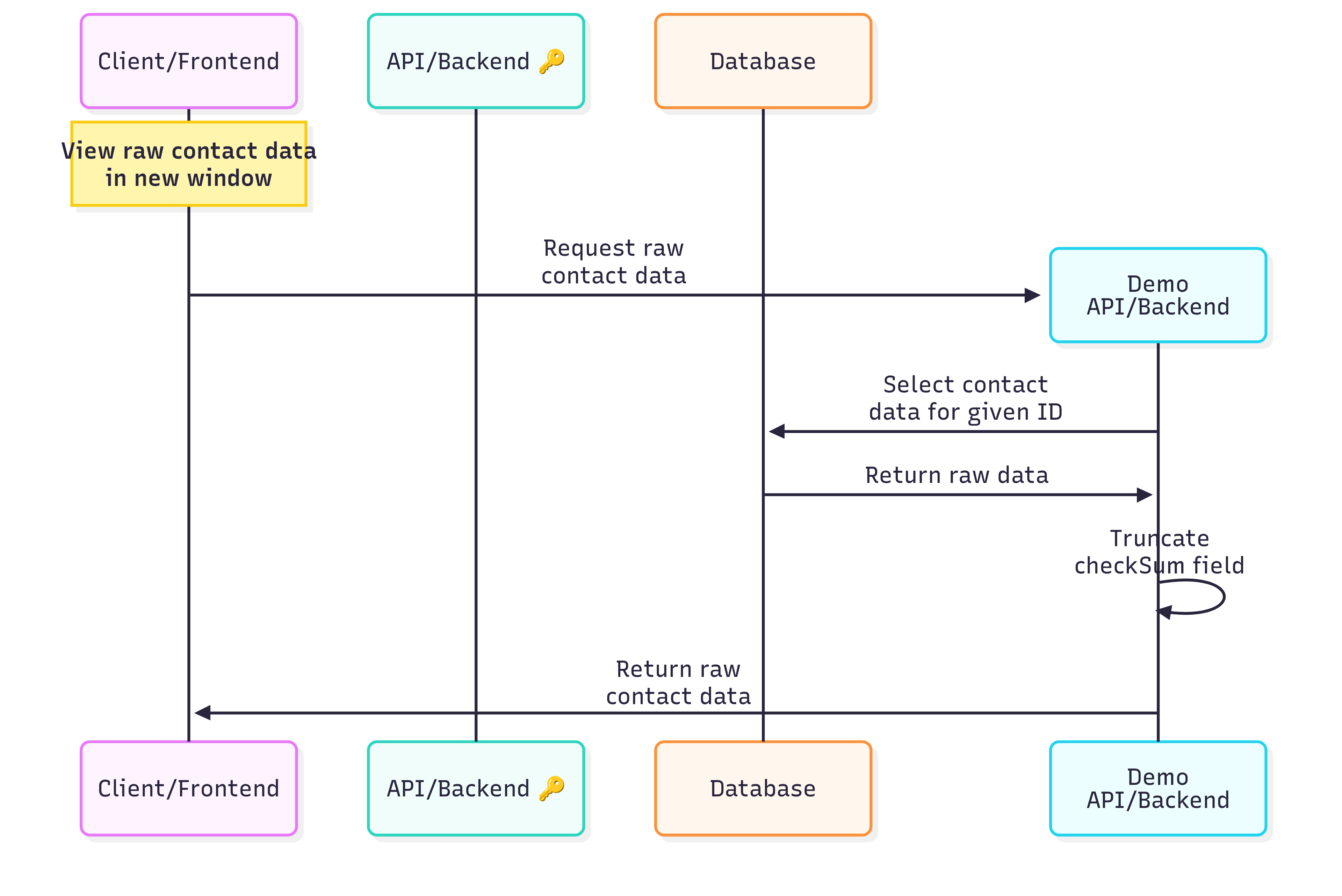
For the curious (or the skeptical), I added a button to the UI that reveals the raw data straight from the database. This uses a separate backend API with no access to the encryption keys. The results pop up in a browser window as raw JSON—decoys and encrypted blobs galore.
For example, here’s the raw data stored for the contact “Crazy Horse”:
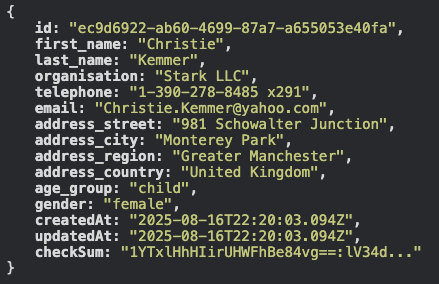
(Data fields for region, country, age group, and gender aren’t faked—they’re still useful for aggregate analysis.)
If you update a contact, the relevant fake data updates too. Add a new contact, and the backend generates fresh decoys before passing the record to the database.
In short: attackers poking around the database get nothing but smoke and mirrors, while legitimate users and integrations enjoy seamless access to the real deal. Security by sleight of hand, in action.
